AutoPi is constantly evolving and improving security, to ensure the safe usage of AutoPi devices. For this, we conduct penetration testing and security audits together with external companies and institutions.
Update: Read our new and improved article about The AutoPi Cloud
Cloud Security
From the AutoPi Cloud, you can access your device remotely. This also means that if unauthorized users have access to your user account, this could be a possible security risk.
Brute forcing into the AutoPi Cloud is virtually impossible due to the use of PBKDF2 for password hashing. Additionally, there is a rate limit on all attempts, so connection attempts are refused after a certain number of attempts.
All our servers are secured with HTTPS protocol, to encrypt data so that logins and data cannot be intercepted and also removes the threat of man-in-the-middle attacks.
The biggest threat to getting access to the AutoPi Cloud is through Social Engineering. The method is characteristic of a physical person attempting to gain access to your password, using either phone or e-mail to impersonate an employee from AutoPi.
This is also why we will never ask for your password at any time. We have several strictly defined workflows with restrictions on what information can be shared with a customer, or a person impersonating a customer, to prevent any social engineering attacks from succeeding.
Unlock the Power of Fleet Management with AutoPi Cloud
Discover the advantages of a comprehensive solution for remote vehicle monitoring, control, and optimization. Streamline your operations and enhance your bottom line by using real-time data tracking and automated software updates.
Start your journey to a smarter, more efficient fleet now!

We also recommend that you always keep your password safe with you and never share it. We recommend that you use a strong password, that is unique to the AutoPi Platform and is changed regularly.
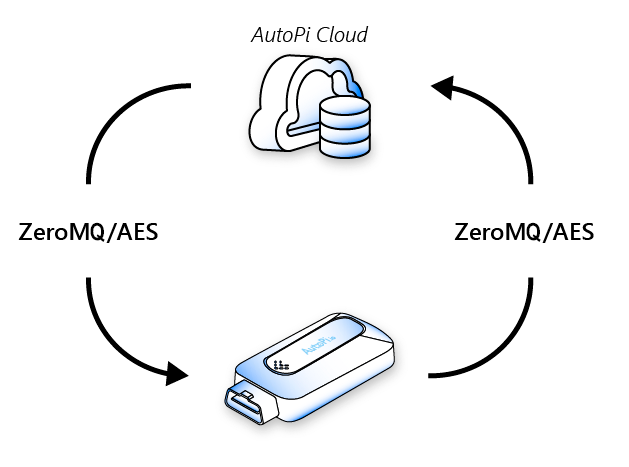
Communication from the AutoPi Cloud to the AutoPi device is performed using ZeroMQ built into the SaltStack platform. Information is pushed from the AutoPi Cloud to the devices, where the AutoPi Cloud initiates all communication to the devices, to ensure a secure one-way connection from the AutoPi Cloud to the device.
Authentication of the devices is performed using device ID and RSA keys. When initially authenticated, all subsequent traffic sent is encrypted using Advanced Encryption Standard (AES). This specific setup prevents any kind of spoofing attacks.
An explanatory visualization of how the AutoPi cloud system works
Device Security
The AutoPi platform is designed to be open and used by users to build custom solutions. This is why the AutoPi is open and accessible by SSH using the WiFi hotspot, built into the device.
Even if the platform is designed with openness in mind, we still value device security highly. This is why the device is preconfigured with firewall rules and security built-in.
Together with KTH Royal Institute of Technology, Stockholm Sweden, we recently had a security audit on our device and this revealed a CVE (CVE-2019-12941) in the device's WiFi hotspot.
Essentially access could be gained to the device by brute-forcing the WiFi hotspot password, in some way similar to what previously was done on WiFi/network devices with a default password supplied by the factory.
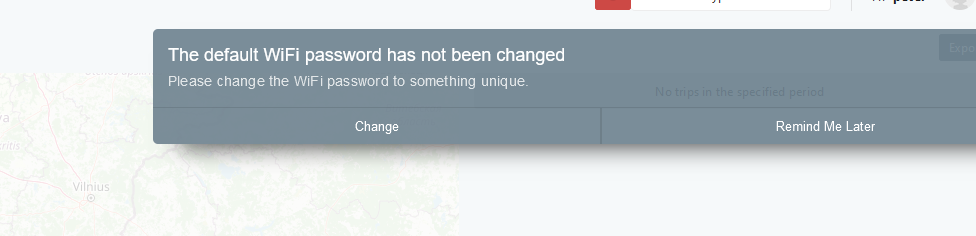
The AutoPi is shipped with a unique default password from the factory, to allow users to gain access to their device as part of our openness/ease-of-use approach.
This is also why we always recommend that you change your default WiFi hotspot password and why you are presented with a reminder every time you log into the AutoPi Cloud.
Security Recommendations
-
Always keep your AutoPi Cloud password secret.
-
Change the default WiFi password.
-
Make sure all passwords are strong.
-
Never share your passwords.
-
Change the passwords regularly.
If you have specific questions about AutoPi security, make sure to get in touch.





