Welcome to our quick guide on CAN Sniffer use. With today's vehicles hosting complex networks, a CAN Sniffer is your key to unlocking and understanding this complex system. Follow our five-step method to start monitoring and interacting with your car's data network efficiently. Let's get started.
Modern cars are controlled by a series of Electronic Control Units (ECUs) - think of these as mini-computers that manage every electrical element in your vehicle.
By connecting a telematics device like the AutoPi CM4 to your car's OBD-II port, you're able to engage with the ECUs, effectively replicating CAN bus sniffer software capabilities.
Communication within these subsystems occurs over a dedicated network called the Controller Area Network (CAN), where they dispatch messages throughout the network. An illustration of a CAN message would be:

The '024' in a CAN message represents the identifier of the transmitting ECU, with the subsequent characters encoding the actual information, such as a command to unlock the vehicle.
Gaining access to the CAN bus allows for the transmission of commands directly to your car, effectively enabling you to insert instructions onto the CAN network. However, pinpointing individual commands for specific vehicle functions is not that simple.
To identify specific commands, one effective technique is to monitor and capture the data flow on the bus while simultaneously performing the desired action in your vehicle, like unlocking the doors. You can then locate the corresponding command within the captured data. Let's get into how it's done.
How To Make a CAN Bus Sniffer To Unlock Doors
Commonly known as CAN bus sniffing or hacking, this technique traditionally requires advanced knowledge to uncover your car's hidden metrics.
Yet, with the AutoPi device, the complexity is significantly diminished. Just a handful of simple steps executed through the AutoPi Cloud can equip anyone with the ability to begin hacking their car's CAN bus, including unlocking doors.
Follow These 5 Steps to Build a CAN Bus Sniffer for Door Unlocking
-
Initiate CAN Bus Discovery: Utilize your CAN sniffer tool to detect the operational CAN buses within your vehicle. This crucial first step sets the stage for the hacking process by identifying the active communication channels.
-
Configure the Vehicle's Profile: Log the medium-speed CAN bus into the vehicle's system profile. By doing so, you establish a foundation for the subsequent steps, ensuring you can interact with the right bus.
-
Capture CAN Messages: While engaging the unlock button on your key fob, record the CAN messages transmitted over the medium-speed bus. These messages are automatically saved to a local file on the AutoPi CAN-FD Pro, capturing the essential data needed for analysis.
-
Test Unlocking Function: Replay the recorded CAN messages back onto the bus. This step is vital to confirm that the captured data includes the correct command to unlock the vehicle's doors.
-
Isolate the Unlock Command: Apply the divide and conquer strategy to sift through the recorded data and isolate the singular CAN message responsible for the unlock function.
With these steps, CAN bus hacking is made simple. Our detailed blog post will look into the specifics and guide you through utilizing your newfound metrics for vehicle control and monitoring.
What is CAN Bus Sniffer Software?
A CAN bus sniffer software is a specialized program designed to intercept and decode communication on a CAN bus. This type of network is prevalent in automotive and industrial control systems. By employing CAN bus sniffer software, technicians and engineers can monitor and decipher the real-time data exchanged within the network.
Such software is instrumental for diagnosing problems, pinpointing faults, and ensuring the network's functionality. Typically, this software works in conjunction with hardware components like an interface and cable, presenting the data in an accessible format, whether it's ASCII or hexadecimal.
Understanding the flow of information with CAN bus sniffer software is crucial for maintaining the health and performance of a CAN bus system.
How CAN Bus Sniffing Tool Works
A CAN bus sniffing tool works by tapping into the Controller Area Network (CAN) of a vehicle, which is the main avenue for communication between various microcontrollers and devices. Here's how it operates:
-
Connection: The tool connects to the vehicle’s OBD-II port, providing access to the CAN bus.
-
Monitoring: Once connected, it begins monitoring the data traffic, capturing every packet that traverses the network.
-
Decoding: The tool decodes the raw data, translating it into a human-readable format. This can include various vehicle metrics such as speed, RPM, and sensor data.
-
Analysis: Users can analyze this data to diagnose issues, understand vehicle performance, or modify the behavior of vehicle subsystems.
-
Interception and Injection: Advanced use involves intercepting specific messages or injecting new ones to alter the behavior of the vehicle, such as unlocking doors or tweaking performance parameters.
The tool's ability to dissect and understand the flow of information on the CAN bus is what makes it a powerful ally for technicians, engineers, and enthusiasts.
To take full advantage of CAN bus data and unlock powerful vehicle insights, the **AutoPi CANFD Pro** is the ultimate tool, designed for professionals who need precision, reliability, and advanced functionality.
How to Use a CAN Bus Sniffing Tool:
Sifting through the dense data on a vehicle's CAN bus for specific messages is a daunting task. The "divide and conquer" method simplifies this by splitting the data into smaller sections for easier analysis.
This iterative process continues until the precise message is isolated, showcasing the practicality of a CAN bus sniffing tool in pinpointing exact data points within the vast network of vehicle data.
Using a CAN bus sniffing tool follows a similar approach. For instance, if your goal is to uncover the command that manipulates the power windows, the steps would be as follows (using AutoPi device):
-
Start by recording the messages transmitted when the window switch is activated.
-
Split the captured messages into two equal parts.
-
Replay the first half of the data to the car's CAN bus.
-
If the windows respond, that half contains the target message.
-
Repeat the halving process with the correct segment.
-
Continue until you isolate the specific message for window control.
-
And finally, after pinpointing the exact command, it’s crucial to replay or send it back to confirm its the correct one.
Below is a 34-line sample from a 1797-line data log, recorded over 5 seconds:

This procedure may seem daunting, but the AutoPi system simplifies the complexity. With its user-friendly interface, the intricate becomes straightforward. The AutoPi system serves as a versatile CAN bus sniffer tool, offering a suite of functionalities designed to make this process as seamless as possible.
The Rewards of Reverse Engineering Your CAN Bus
Looking into the Controller Area Network (CAN) bus through reverse engineering unveils numerous rewards, offering enhanced insights into vehicle diagnostics and system optimization. Let's explore a few examples:
-
Deepen system understanding: Dive into the vehicle's communication systems for detailed component interactions.
-
Diagnose with precision: Dissecting the CAN bus allows for sharper, more efficient troubleshooting.
-
Customize for improvement: Modify system behaviors for enhanced performance or new features.
-
Strengthen security: Use it to proactively find and fortify network vulnerabilities.
-
Drive innovation: Use insights gained to innovate and craft new tech solutions.
-
Save on costs: Avoid pricey proprietary tools for more economical maintenance.
-
Learn practically: It’s a valuable, practical learning tool for embedded system education.
Embarking on the journey of CAN bus reverse engineering not only equips you with a abundance of practical vehicle hacks but also sheds light on why it's often referred to as CAN bus hacking. There's a wealth of knowledge to be explored, and the benefits are just waiting to be unlocked.
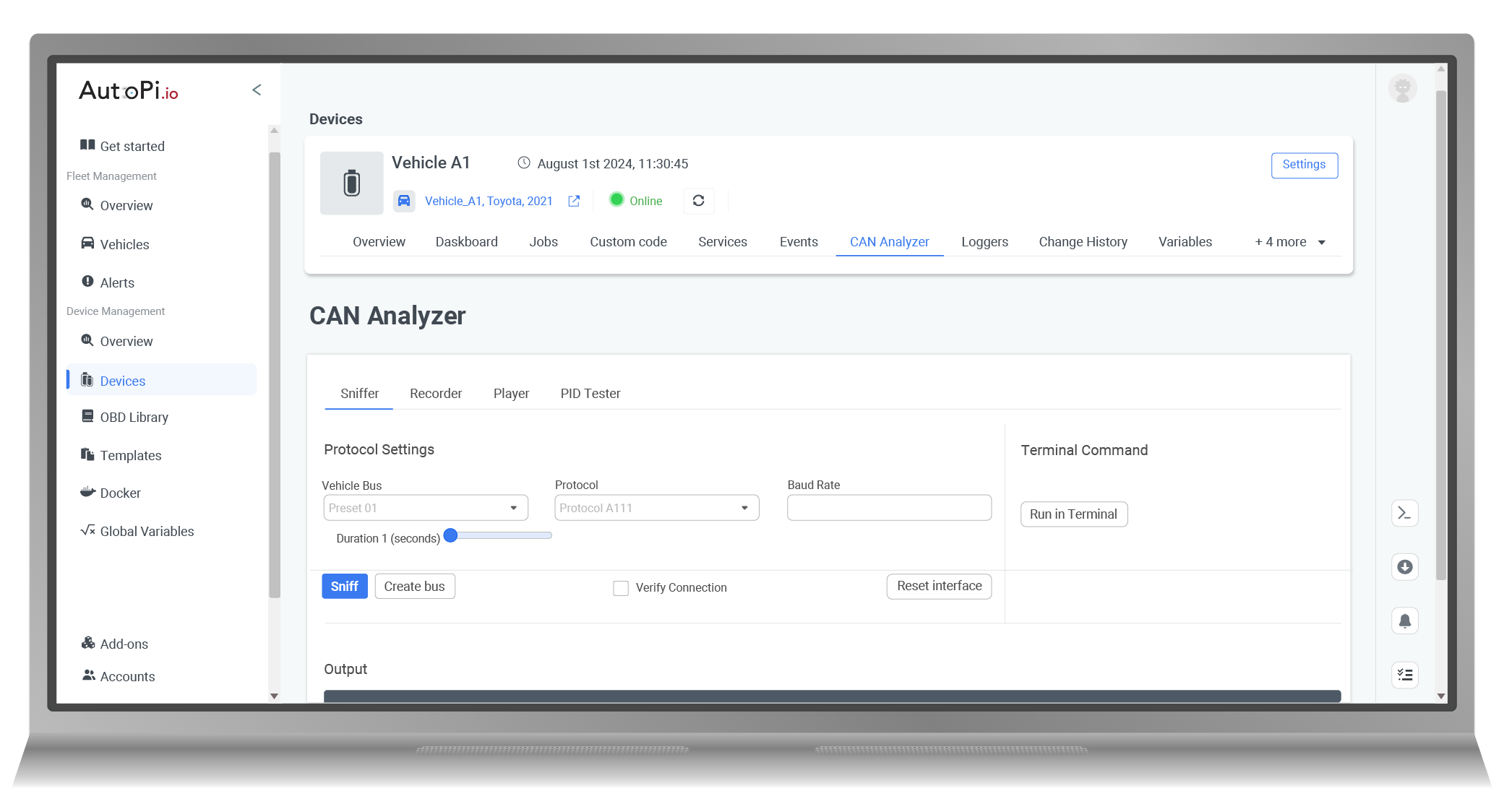
Unlocking Car Commands with AutoPi Device
The AutoPi Device, together with the AutoPi Cloud, streamlines the once-complex task of identifying your vehicle's CAN commands into an intuitive, automated user interface.
Here's how to tap into new CAN commands with AutoPi:
-
Connect with CAN Explorer: Start by accessing the CAN explorer to establish a connection with your car.
-
Start Recording: Hit the record button and then execute the desired function in your car, such as unlocking the doors, five times to ensure accuracy.
-
Stop and Analyze: After recording, press stop. The platform will process the data and suggest possible commands.
-
Test and Save: Experiment with these commands to find the right one. Once confirmed, hit save to keep the command for you and others to use.
Deciphering raw CAN messages can be daunting, especially for newcomers. That's why we've crafted a guide to assist you in logging these messages with ease. Access the guide here.
After finding the new command, the AutoPi system will sync it to your device, ready for real-world application.





